- Accueil
- hacker gadget
- Jinwook Kim on X: [Tool] The-Hackers-Hardware-Toolkit : The best hacker's gadgets for Red Team pentesters and security researchers. / X
Jinwook Kim on X: [Tool] The-Hackers-Hardware-Toolkit : The best hacker's gadgets for Red Team pentesters and security researchers. / X
4.7 (334) · € 39.50 · En Stock

PDF) A Systematic Literature Review on the Cyber Security

VPN Url, PDF

Decentralize All The Things: Deploying Your Own Node Infrastructure · Devcon Archive: Ethereum Developer Conference
Public Resumes: Job Profile Builder
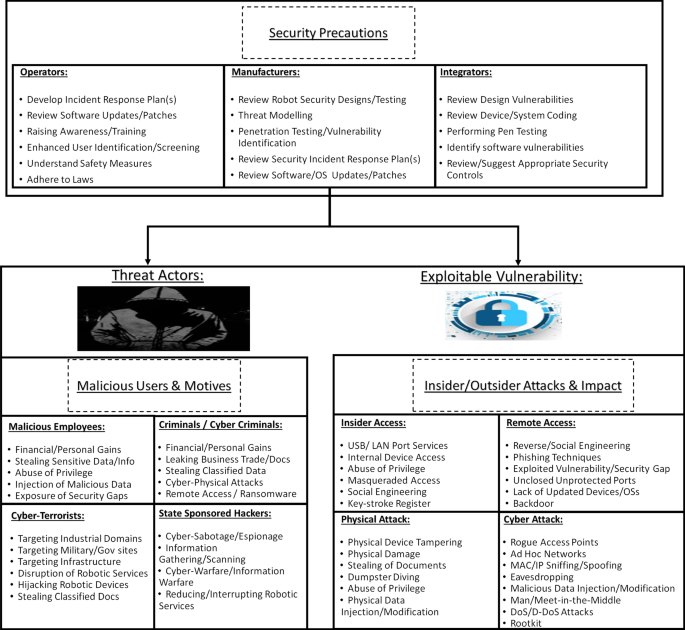
Robotics cyber security: vulnerabilities, attacks, countermeasures, and recommendations

Decentralize All The Things: Deploying Your Own Node Infrastructure · Devcon Archive: Ethereum Developer Conference
Readability-Resources/cyberDictionary.txt at master · SP2-MC2/Readability-Resources · GitHub
Public Resumes: Job Profile Builder

14 Best Hacking Books (Definitive Ranking)

Internet of Things backdoors: Resource management issues, security challenges, and detection methods - Hashemi - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

Do hackers think it is easy to hack someone? If not, why? - Quora

VPN Url, PDF

Decentralize All The Things: Deploying Your Own Node Infrastructure · Devcon Archive: Ethereum Developer Conference






/cdn.vox-cdn.com/uploads/chorus_asset/file/24108884/226349_Flipper.jpg)





![Jinwook Kim on X: [Tool] The-Hackers-Hardware-Toolkit : The best hacker's gadgets for Red Team pentesters and security researchers. / X](https://pbs.twimg.com/media/D7S-2o4X4AEGzcn?format=jpg&name=4096x4096)