Proposed protocol simulation in presence of the intruder.
4.8 (232) · € 29.50 · En Stock

Modeling and verifying NDN‐based IoV using CSP - Chen - 2022

Enhancing the Elliptic Curve Integrated Encryption Scheme in 5G
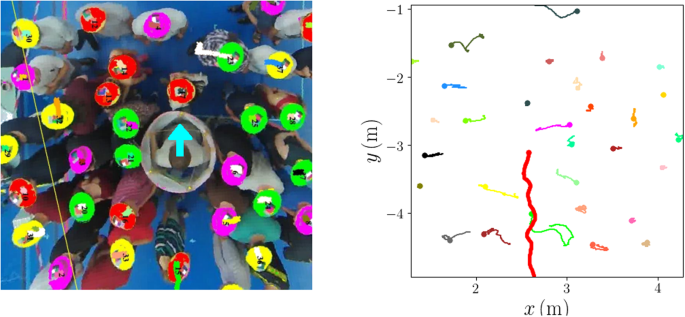
Mechanical response of dense pedestrian crowds to the crossing of

Intruder simulation of case 1 in AVISPA using CL-AtSe

Introduction into SkyRadar's Breach, Attack and Defense Simulator

A review and analysis of secure and lightweight ECC‐based RFID
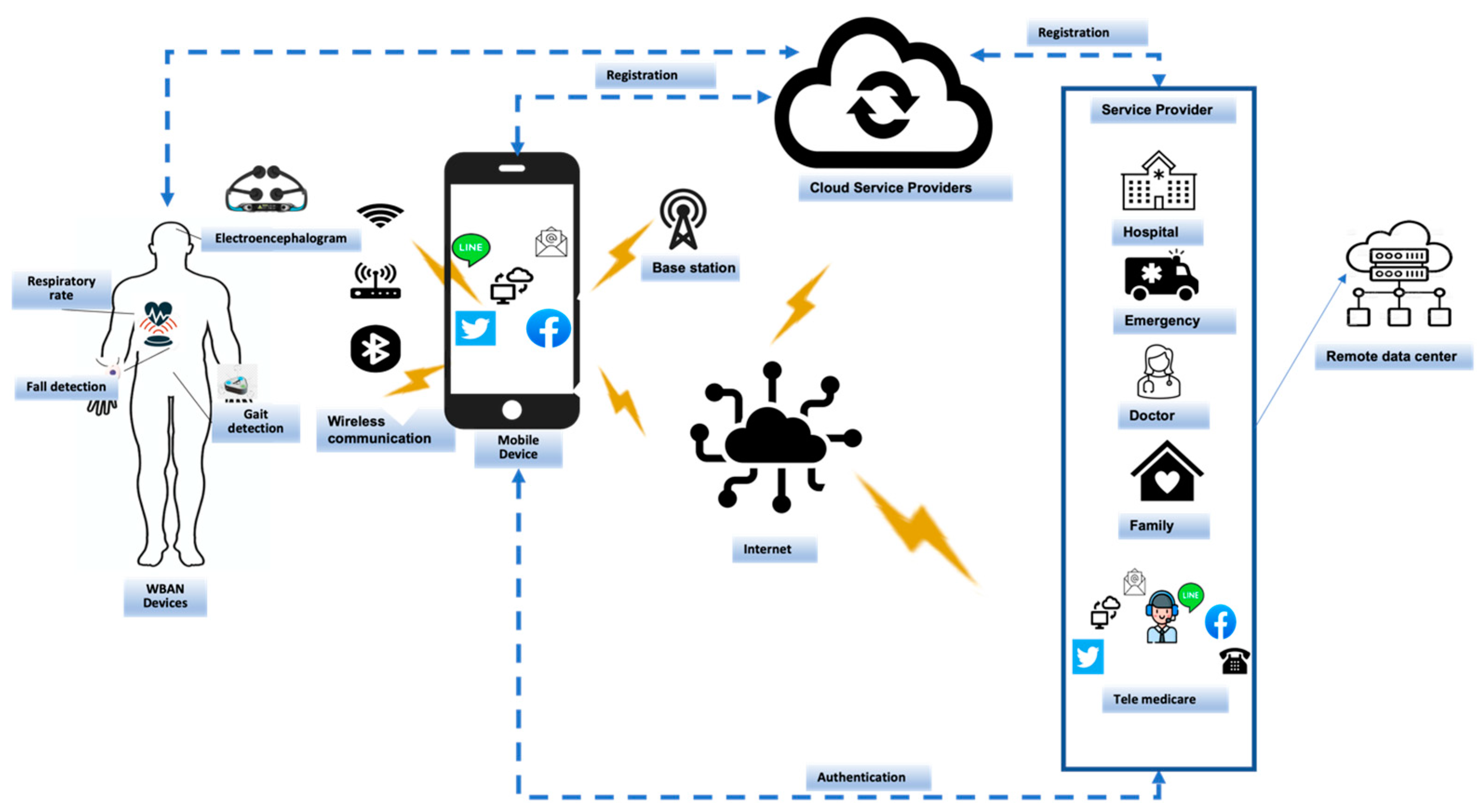
Electronics, Free Full-Text
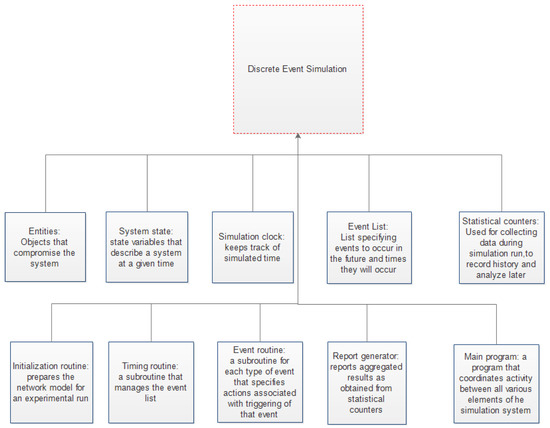
Telecom, Free Full-Text

Secure intrusion detection system routing protocol for mobile ad

A new estimator for the multicollinear Poisson regression model
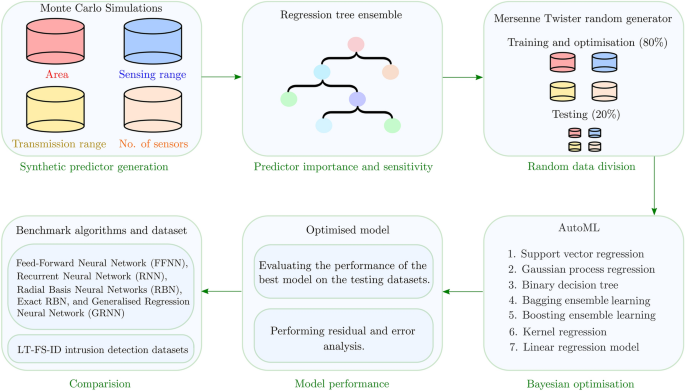
AutoML-ID: automated machine learning model for intrusion

A novel approach for securing data against adversary attacks in

Basic animation with the intruder, the intruder may take advantage
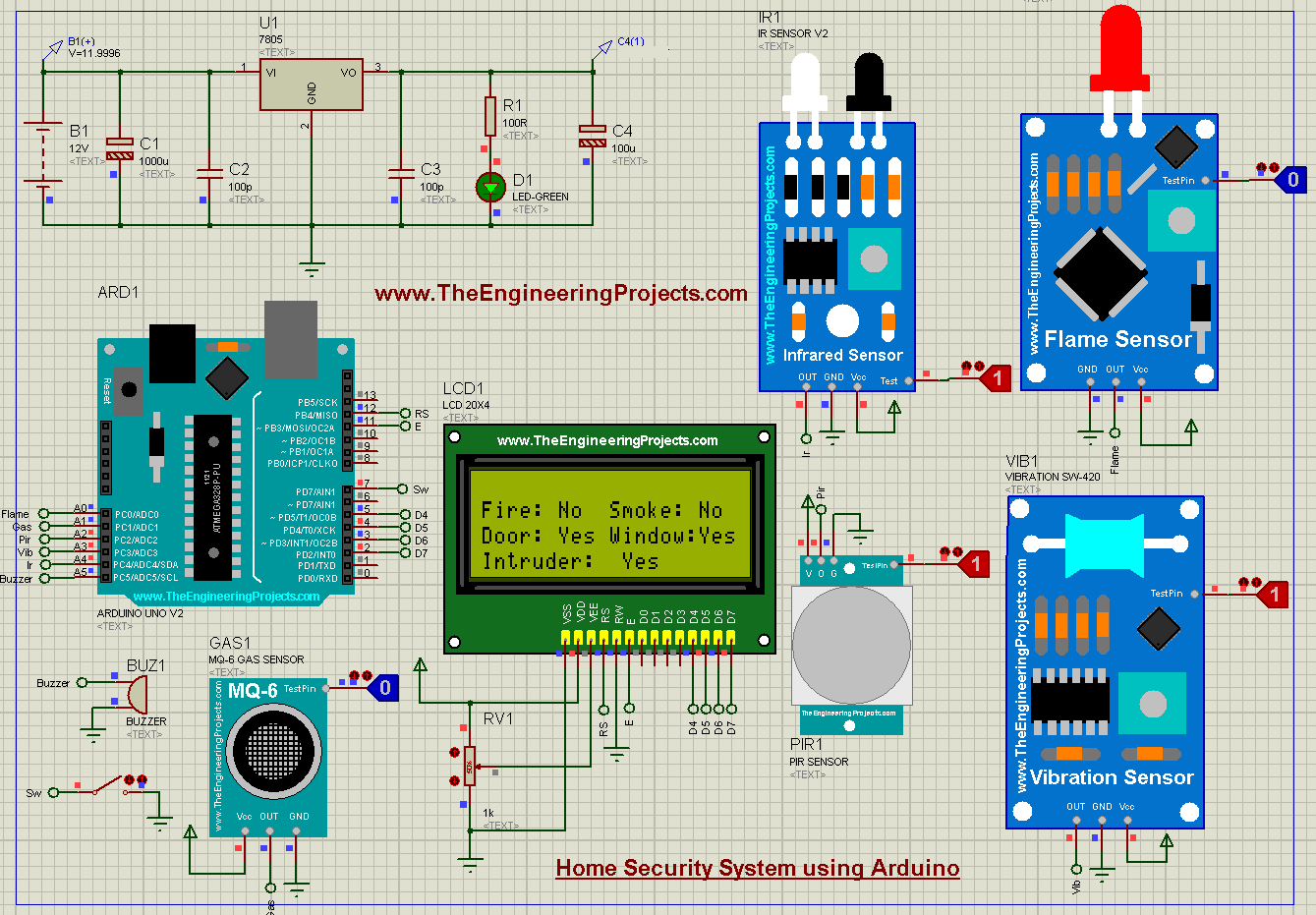
Home Security System using Arduino UNO in Proteus - The

Alice sends the secret nonce-3